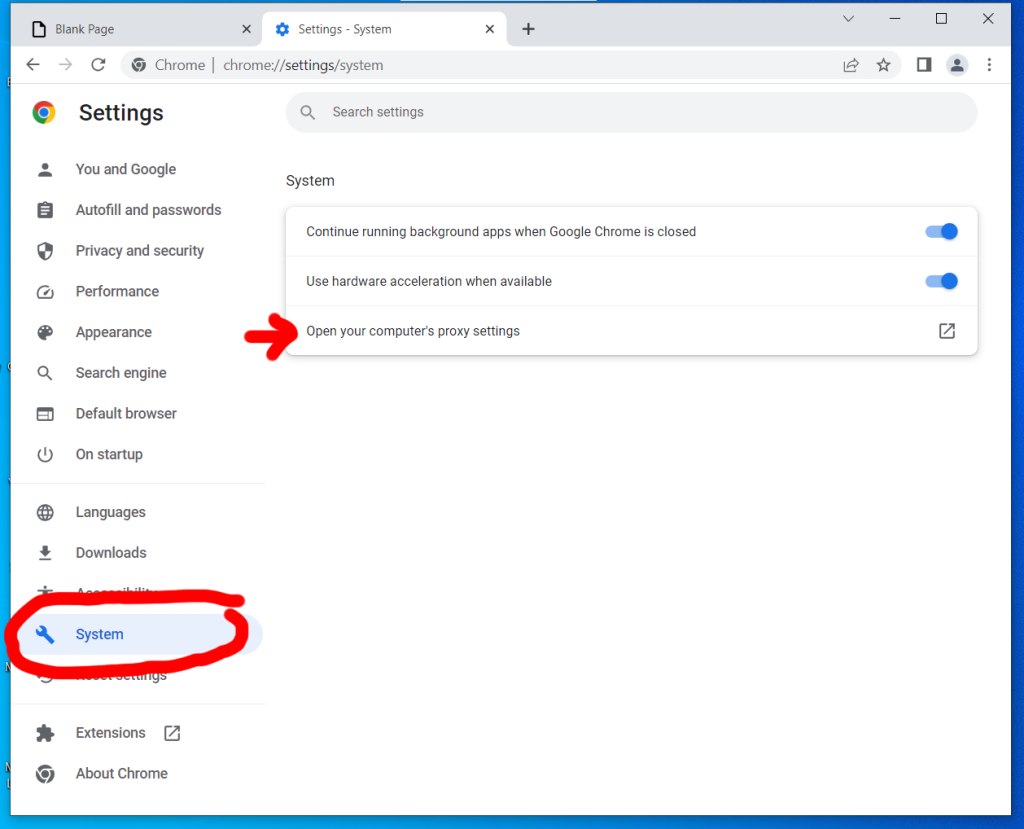
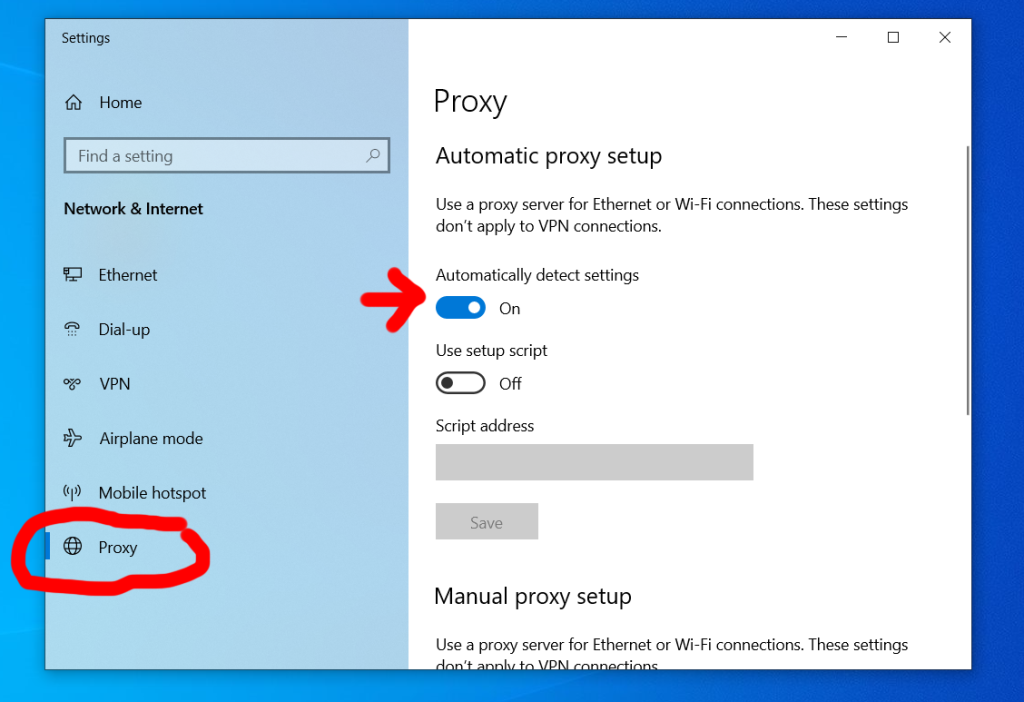
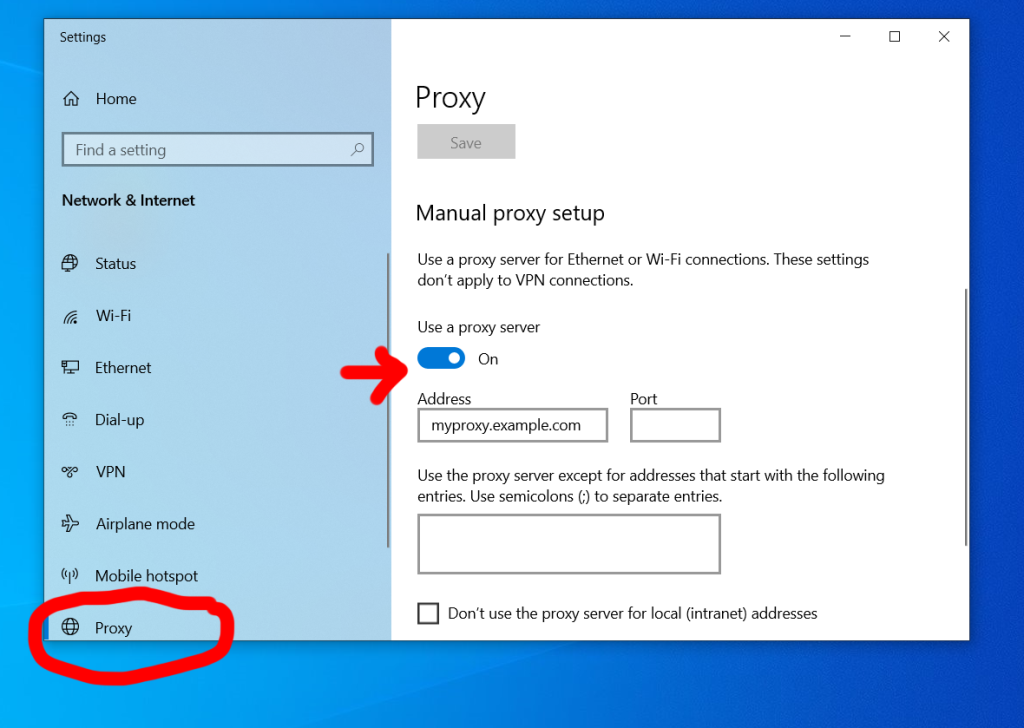
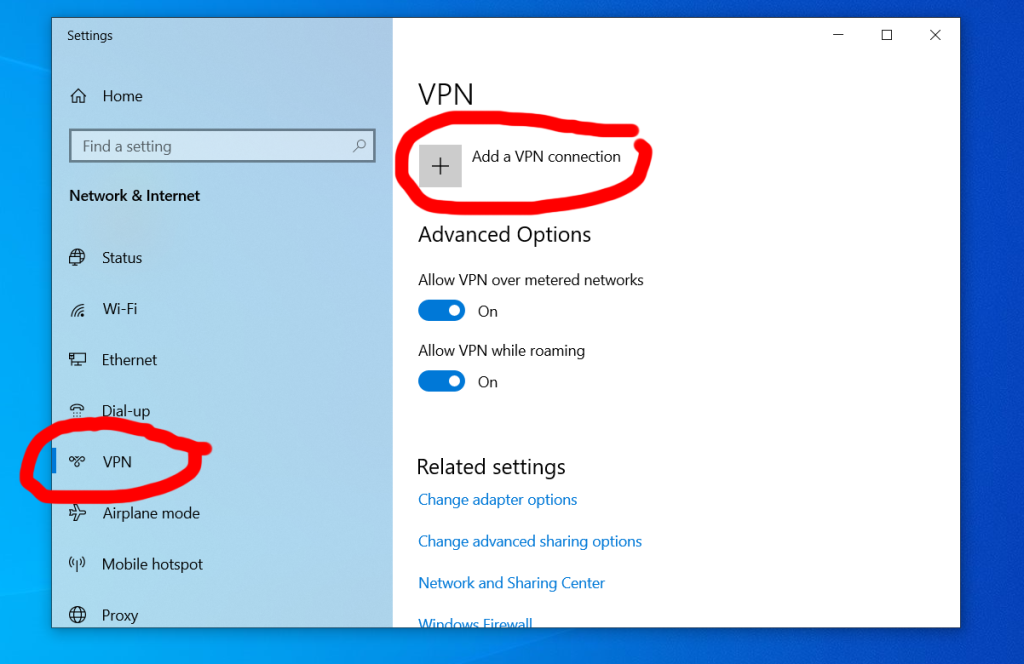
Who isn’t on social media these days? 60% of the global population and 93% of all internet users use social media apps. You may have never imagined your grandma would get decorating ideas before you do on Pinterest, but it’s happened.
It’s given us unparalleled opportunities to stay connected but it’s also made maintaining our online privacy a bit complicated.
We grew up with cautionary tales of how famous people like Michael Jackson, Elvis, and Marilyn Monroe were driven to the edge by the loss of their privacy. Of course, we never thought normal people would face the same challenges on a smaller scale.
Most people who are doing something enterprising or of public interest need to market themselves, whether they’re entrepreneurs, politicians, musicians, or authors. If you want to succeed, it’s part of the game. But that doesn’t mean you can’t keep your private life private.
Here are key privacy mistakes that can be easy to make on social media. Do your best to avoid them and sleep soundly knowing you’ve done your part.

You reveal personally identifiable information
Many mistakenly believe that because they don’t have a high profile on social media, have low income, or have bad credit, identity theft isn’t something to be concerned about. It is!
Today’s bad guys are organized, savvy, and they’ve got incredible tech at their disposal. You might not think it’s a big deal to reveal your email address, your username, or another small piece of information that’s associated with your identity. Remember that criminals can potentially build databases to piece together information over time.
Generally, avoid posting documents issued to you by governments, institutions, or businesses online. Leaking small pieces of personal data such as account numbers, or even your mailing address can come back to haunt you one day and it’s commonly done. In fact, according to a study by Experian, Americans have posted an average of 3.4 pieces of sensitive information online.

You overshare about personal events
Oversharing can mean many things. It can mean getting into an emotionally-charged state and posting about one’s personal drama. It can mean talking poorly about your ex or your former employer and getting into detail about past experiences.
It’s a tougher issue than it might seem because we bond with others by sharing things about ourselves, including our vulnerabilities.
If you post regularly on social media you have to reflect and be honest with yourself. Determine which parts of your life you’re comfortable with being public knowledge and which parts you prefer to keep private. Once the cat’s out of the bag there’s no going back.
Some people are proficient at discovering dirt about people and then spreading gossip. That’s not something you have control of, but don’t make it easy for them by creating a record that can be repurposed as ammunition.
Remember that many are generally unsympathetic to the problems of others. Tell the few you most trust your personal news to get it off your chest and leave it at that.

You reveal your exact location
Geotagging is incredible from a technological perspective. People who are interested in the happenings in an area can tap on the location and see related posts. Thus, it adds to the discoverability of your content.
If overused, geotagging gives people a way to track your activities. More and more it’s being used with precision so that people know which neighbourhood you’re in, right down to the restaurant you’re dining at.
Use geotagging judiciously. You can flex some by letting your followers know you’re visiting New York City without naming the bagel shop.

You post photos of your children publicly
The average parent posts nearly 1,500 pictures of their child online before age five according to a study by Nominet.
Parents are proud of their kids. They’re a huge part of their world, and that’s wonderful. However, sometimes we have to remind ourselves that Instagram isn’t a family photo album.
Ever heard the term “sharenting?” It’s when parents publicize personal information about their child online. People wouldn’t imagine sharing detailed private information about their friends online, but “sharenting” is incredibly common. And it’s usually done without permission by the child.
Many parents don’t think about it, but a photo or video that is funny or cute might not be seen the same in the future. At best, it will be slightly embarrassing to your child. At worst, it could negatively impact their reputation later in life.
When we post content publicly, we create a record that can be accessed by people with bad intentions and by automated technologies. It opens your child up to risks such as facial recognition tracking, online security threats, and worse.

You accept friend requests from strangers
Bots and people who are pretending to be someone else (aka catfish) are incredibly common on social media.
Platforms like Facebook give you the opportunity to approve or deny friend requests. Not much good can come of adding someone you don’t recognize. Adding them could expose you and your friends to online security threats, scams, surveillance, and misleading information.

You share information about people without their permission
Social media tends to polarize people these days. One camp believes in the power of personal branding. Their careers depend on putting themselves out there online. The other camp is known to launch into rants about how social media is destroying the fabric of society.
There are a million and one reasons someone wouldn’t want you to post a group shot with them in it on social media. It’s best to never make assumptions. Let people know if you plan to post something about them online so they can opt out.
Posting photos or information about people could have ramifications for them you didn’t consider, whether it’s at their job or in their marriage. It might not strike you as fair or reasonable but you don’t want to be blamed for sparking a conflict.

You don’t use audience selection features
Want to share a story about your career journey but don’t want your ex-employer to see it? Some social media content falls into a gray area in terms of privacy decisions. Luckily, there’s a middle ground in-between public and private posts.
Apps like Facebook and Instagram allow you to create lists of people and deliver content to that audience only. Sometimes you can exclude people or a list of people from seeing a post or story as well.
For example, Instagram allows you to make a “Close Friends” list. And on Facebook, you can add people to your list of “Acquaintances.”

You don’t remove bots and fake accounts that follow you
On Platforms like Facebook and LinkedIn housecleaning your list of connections is easy because both sides have to agree to connect out of the gate.
It’s trickier to manage your followers on apps like Instagram and TikTok when you have a public account. It’s an ongoing process.
Every now and again, check your follower list and remove suspicious accounts. With practice, you’ll see patterns and it’ll be easy to spot certain types of fake accounts and scammers. In many cases, it won’t be clear what their objective is. But if there are clues that it isn’t a real person, it’s best to remove them rather than ignore them.

You don’t manage your tagged photos
Social media apps don’t have many restrictions when it comes to who can tag you in photos. In fact, on apps like Instagram spammers will tag you just so you’ll look at their post. And no, the image never has anything to do with you.
When potential employers or potential dates start digging through your profile, tagged photos are the first things they look at.
There are bound to be photos you’re tagged in that don’t send the right message. Take the time to check it every now and again, and remove your tag from the not-so-flattering shots, or the photos that reveal personal information you’re not comfortable with sharing with everyone.

You take questionable online quizzes
Facebook quizzes were huge back in the early days of the platform. People installed apps just to find out which character they are in Friends.
Quizzes seem like a fun and harmless way to share your personality traits with your friends. The problem is that the people who complete them usually don’t know who’s gathering their data and for what purpose.
If you think about it, quizzes are the perfect way for shady developers to extract data from people such as their name, birthdate, and other personal information. It doesn’t seem like much of a threat until you consider it can be pieced together and used for nefarious purposes.

You don’t use privacy settings and features
Every major platform has privacy features, and they usually go way beyond the ability to make your account private.
From hiding Likes on your post to limiting commenting to people you follow, social media apps allow you to use a lot of nuance when it comes to privacy. Experiment so that you’re confident in deploying privacy features when they’re most needed.
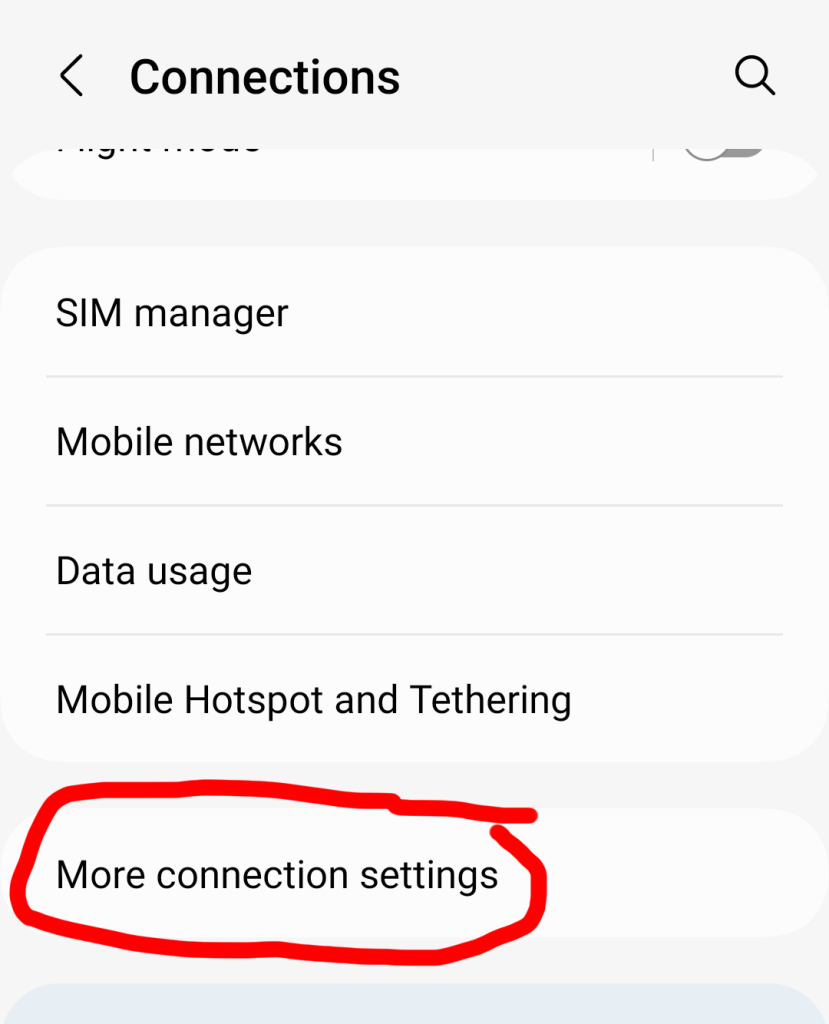
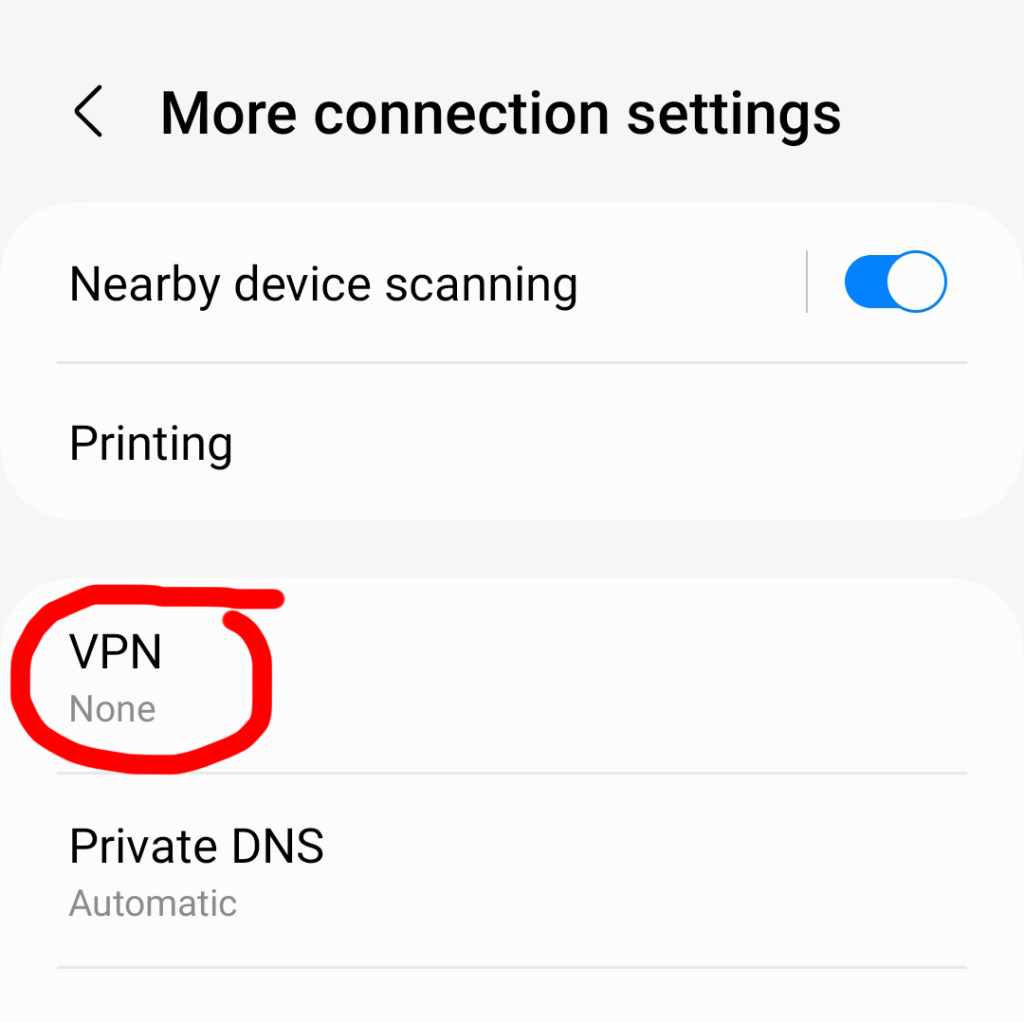
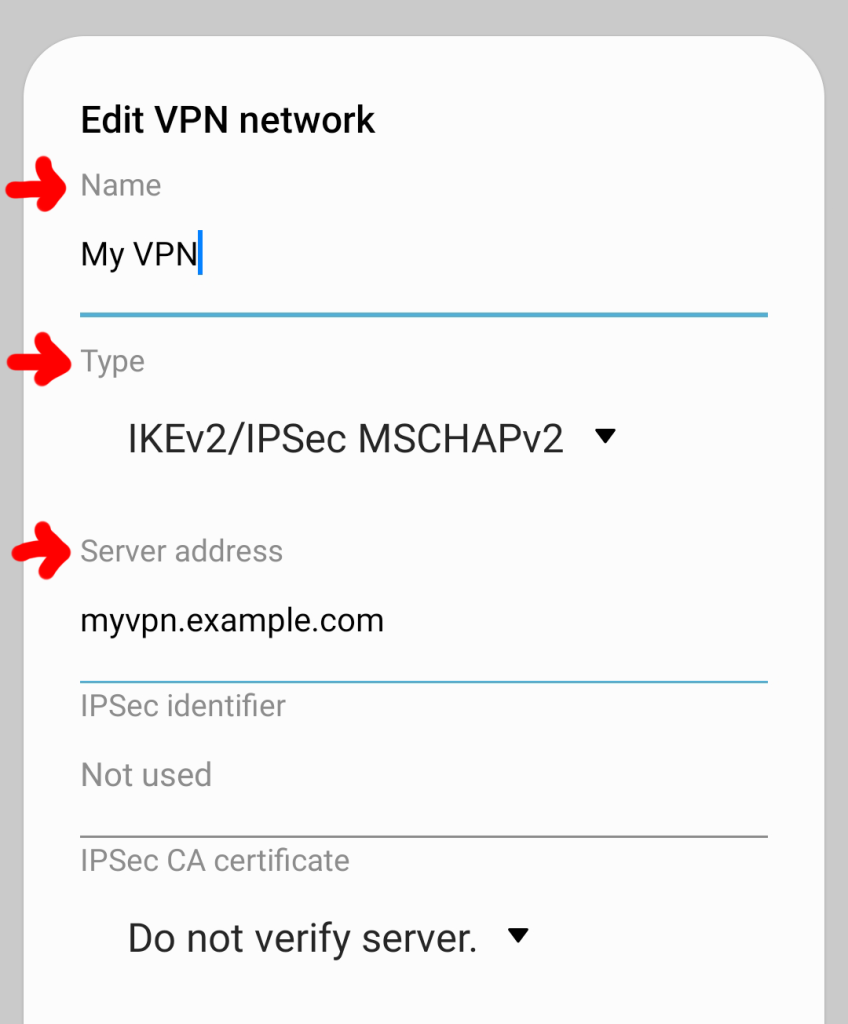
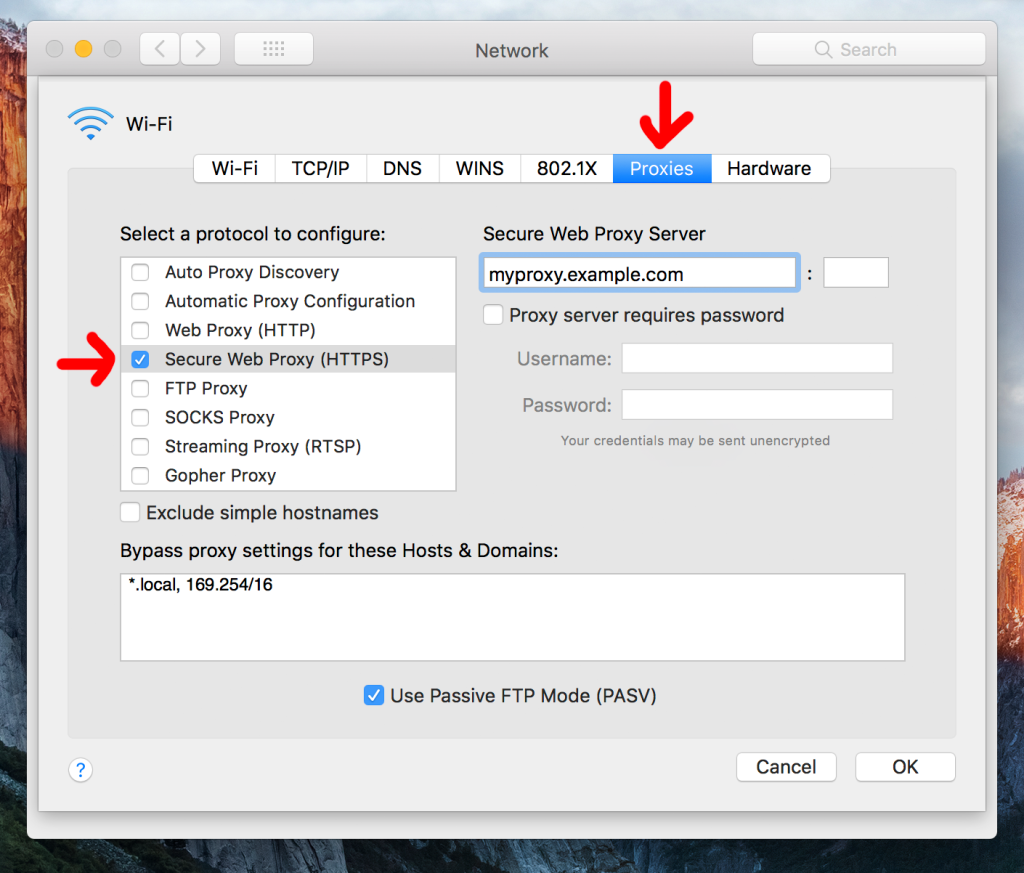
One of the key areas to investigate is the permissions the app has to access the data on your phone. Check its level of access to your photos, videos, location data, your mic, etc.
Location, camera, and microphone permissions can be set to “All the time,” “Allow only while using the app,” “Ask every time,” or “Don’t allow” on Android. There are no right or wrong answers here except that it makes sense to have stricter privacy settings on features you rarely use or don’t use.
Blocking access can break functionality in the app. So, test it before deciding how to approach your permission settings.
Conclusion
Let’s be clear, social media has plenty of benefits. Your online privacy is important but so is connecting with other amazing humans.
The key is to remind yourself of these privacy pitfalls before you hit the post button. Sometimes it’s easy to get caught up in the moment and reveal too much.
I hope you leave this article with some takeaways that will make your online journey a bit smoother. Stay safe!













 Step 3
Step 3